Drones have transformed industries from agriculture to logistics, but they have also become tools for criminals, terrorists and spies. By analyzing the digital trails left by drones, controllers and associated devices, law enforcement can not only solve crimes but also anticipate and thwart future threats. As drone technology evolves, so must the forensic techniques used to investigate their misuse.
The rise of criminal drone use
Drones have become a go-to tool for criminals because they are affordable, mobile and can operate anonymously. They have been used to smuggle drugs across borders, deliver contraband into prisons and conduct reconnaissance for crimes ranging from burglaries to organized trafficking. For example, in Ohio, a network used drones to drop cell phones and narcotics into prisons. Forensic analysis of intercepted devices revealed GPS flight logs that led investigators to the operators’ staging areas. [1]
Similarly, reconnaissance drones have been captured near critical infrastructure and military installations, exposing their use in espionage. [2] These incidents underscore the growing sophistication of drone misuse and the critical need for law enforcement to adapt.
| RELATED: America’s drone blind spot and the 9/10 moment we’re ignoring
Digital forensics as a counterintelligence tool
The role of drone forensics extends beyond criminal investigations. In counterintelligence, captured drones provide valuable insights into adversaries’ operations. Drones intercepted near sensitive installations often contain reconnaissance data. For instance, at Ramstein Air Base in Germany, forensic analysis of a captured drone suggested espionage activities. [3]
Controllers and connected devices store log-in credentials, communication logs and metadata, which can offer critical leads. By examining drones used in terrorist activities, law enforcement can address immediate threats and predict and prevent future attacks.
Proactive vs. reactive drone identification
Traditionally, investigators rely on reactive methods, extracting data after drones are captured. While effective for evidence collection, this limits real-time intervention capabilities. DroneTrace is an innovative identification tool using RF-based electronic fingerprinting that shifts this paradigm by enabling real-time drone identification.
DroneTrace revolutionizes drone management with its unique ability to detect drones during malicious active operations. It analyzes drones’ RF characteristics to create distinct “fingerprints,” allowing real-time tracking without physical capture.
The advantages are significant. Authorities can intervene during ongoing crimes or breaches, distinguish between multiple drones in the airspace and identify unregistered or spoofed drones. This proactive approach enhances situational awareness and optimizes resource allocation.
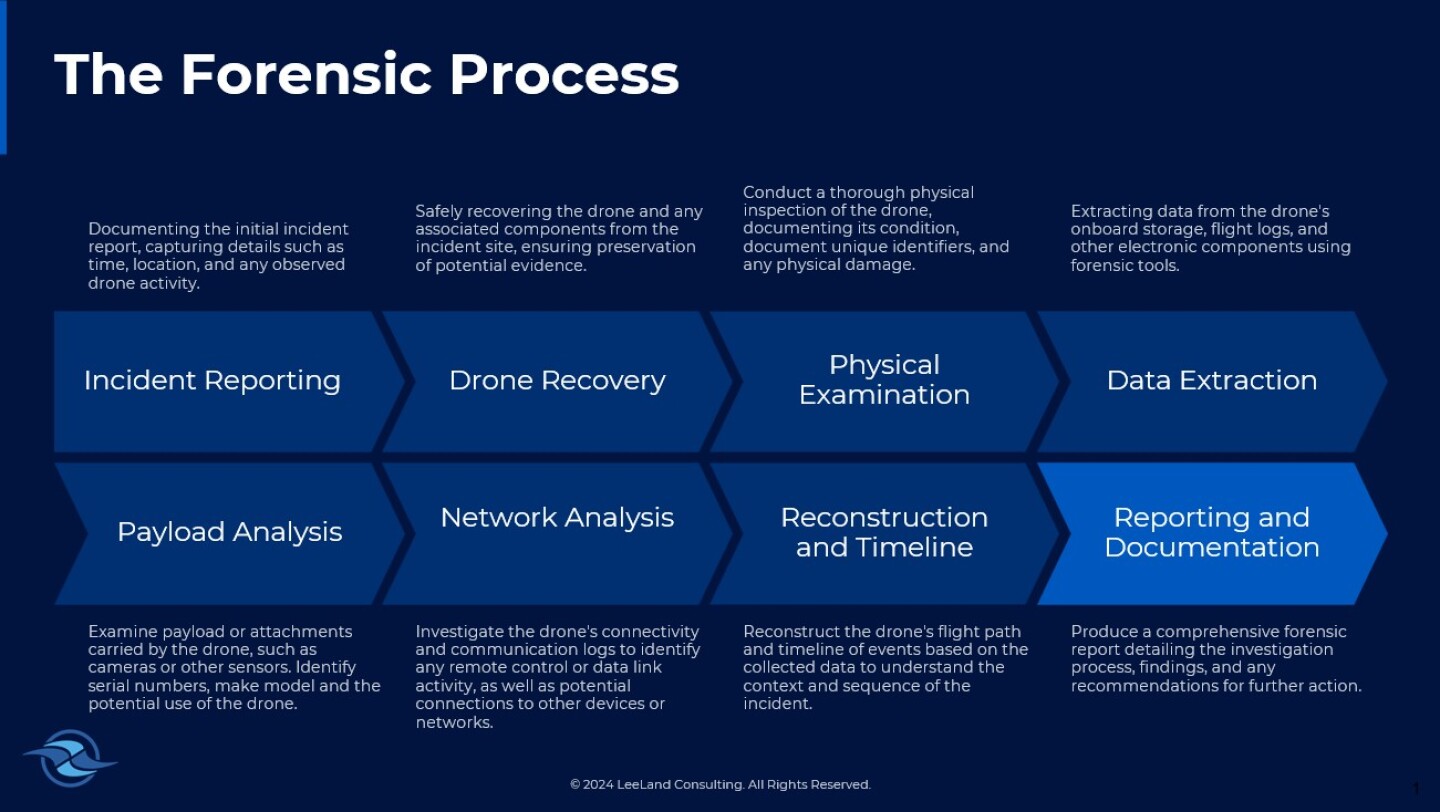
Digital forensics: Extracting evidence
Drones contain valuable data, including from GPS systems, cameras, communication modules and internal storage, recording every movement and interaction. Forensic investigators may use this information to reconstruct events, identify operators and link devices to broader networks.
Drones communicate with controllers using radio frequencies, cell phone bands, Wi-Fi or Bluetooth, transmitting commands and telemetry. Advanced models often use encrypted communication protocols to protect this data. Forensic tools may be able to decrypt and retrieve these stored transmissions from damaged devices.
Critical information recovered from drones can include flight logs, multimedia files, communication logs and metadata. Flight logs reveal GPS waypoints, time stamps and altitude data, while recovered multimedia files provide visual evidence. Metadata, such as serial numbers and geotags, can link a drone to its operator. For example, in Southern California, a fentanyl-smuggling drone revealed critical data linking its operator to an organized network. Forensic analysis of flight logs and video footage enabled investigators to dismantle the operation, highlighting the effectiveness of these tools. [4]
In addition to drones, their associated devices — such as controllers, cell phones, tablets and computers — may hold significant forensic value. Forensic examination of these devices often uncovers connections to broader criminal networks. [5]
These devices often store:
- Command logs: Records of instructions sent to the drone.
- Mobile app data: Log-in credentials, flight histories and user profiles.
- Social media links: Evidence of drone-related activities shared or coordinated online.
Digital forensics: Uncovering evidence
The wealth of digital data generated by drones, often stored on the drone, its controller or connected devices, is invaluable for law enforcement investigations. To understand the significance of drone forensics, it is essential to explore how drones operate and communicate.
- Communication with controllers: These connections allow the operator to issue commands, such as setting flight paths or triggering payload deliveries. Advanced drones use encrypted communication protocols to secure data transmission, which forensic analysts must decode during investigations. Understanding these communication links can help trace the operator’s location and identity.
- Data transmission and storage: Many drones transmit real-time video feeds and telemetry data to their controllers or associated mobile apps. This information is often stored locally on the drone’s internal memory or externally on SD cards, as well as on connected devices like smartphones, tablets or cloud storage platforms. Forensic tools like Cellebrite’s Pathfinder, Oxygen Forensic Detective and DJI Assistant can retrieve this data even from encrypted or damaged systems.
- Artifacts extracted from forensic analysis:
- Flight logs: GPS waypoints, time stamps, altitude and velocity data that reconstruct the drone’s movements.
- Multimedia files: Photos and videos captured during flights that may include visual evidence of crimes.
- Communication logs: Data exchanged between the drone and the controller, revealing commands and operational details.
- Metadata: Information such as device serial numbers, software versions and geotags that link the drone to its operator.
By analyzing these artifacts, investigators can reconstruct the drone’s journey, identify launch and landing points and connect the device to its operator. For example, in the California smuggling case, GPS logs revealed the drone’s flight path, enabling law enforcement to locate the staging area.
Digital forensics as a counterintelligence tool
In addition to solving crimes, drone forensics is a critical asset in counterintelligence. When drones are captured or crash near sensitive areas, the data they contain can offer valuable insights into adversaries’ operations and intentions:
- Gathering intelligence from captured drones: Drones recovered near military installations or critical infrastructure often contain flight paths and surveillance data. Forensic analysis can uncover reconnaissance patterns, target preferences and potential plans for sabotage or attacks. The craft intercepted near Ramstein Air Base revealed detailed images of restricted areas.
- Building profiles of operators: Forensic analysis can identify user profiles, log-in credentials and communication logs stored on controllers or associated mobile devices. These findings help with law enforcement mapping of networks, revealing accomplices or organizations involved in drone operations.
- Preventing future threats: By analyzing the data from drones used in terrorist plots, investigators can uncover broader networks and anticipate future attacks.
- Applying forensic findings to investigations: The data extracted from drones can be instrumental in advancing investigations. By correlating drone forensics with traditional investigative methods, law enforcement can develop comprehensive cases against suspects. For example:
- Tracing launch sites: GPS waypoints and flight logs can identify where a drone originated, leading investigators to suspects’ locations.
- Linking devices: Metadata and communication logs can connect drones to specific controllers or mobile devices, establishing a chain of evidence.
- Identifying accomplices: Communication records may reveal collaboration among multiple operators or connections to organized crime or terror networks.
In the Ohio prison smuggling case, forensic data not only uncovered the drone’s activity but also led to arrests and the seizure of additional contraband. [1]
Methods for capturing suspect drones
Suspect drones come into law enforcement custody through various means, each presenting unique challenges, requirements for legal scrutiny and opportunities for evidence preservation. The following methods may be experienced in your investigation:
- Crashes: Drones that malfunction midflight or are intercepted by counterdrone measures often retain intact data. These incidents require immediate action by law enforcement to secure the crash site, prevent tampering and preserve evidence. For instance, in 2022, a crashed drone carrying contraband into a prison in Texas led to the discovery of its operator through analysis of its onboard flight logs and metadata. [6]
- Search warrants: When investigators can establish probable cause, search warrants allow the seizure of drones and associated devices, such as controllers, storage media and related equipment, from suspects’ properties.
- Abandoned devices: Operators may discard drones to avoid detection. Law enforcement must carefully navigate legal boundaries when recovering these devices, particularly in areas with privacy concerns or contested property rights.
- Proactive countermeasures: Increasingly, law enforcement agencies are studying counterdrone technologies such as net-based systems, signal jammers and, right out of science fiction, directed-energy tools to intercept active drones. These tools enable safe recovery during live incidents, preserving onboard data for forensic analysis. [7]
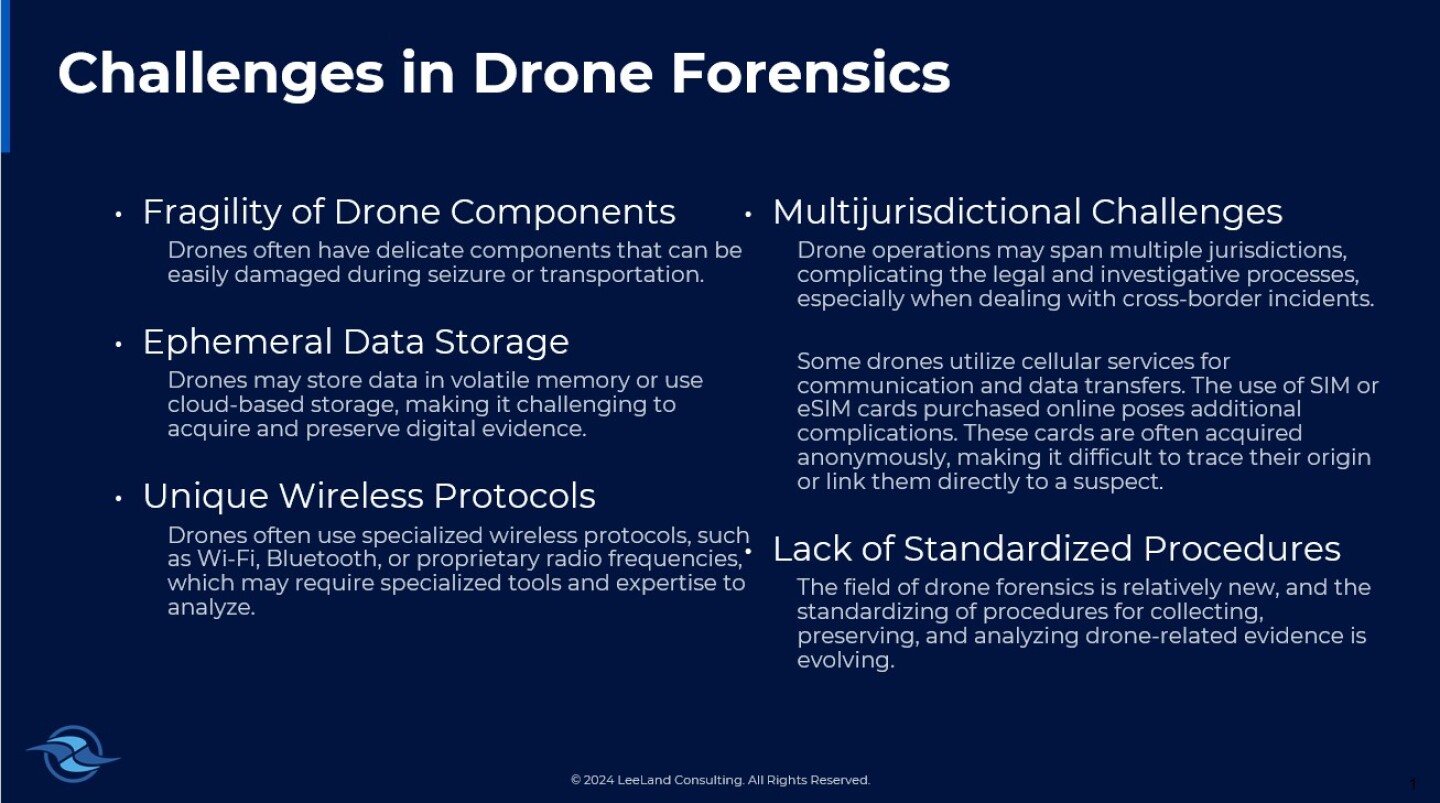
Legal challenges in drone forensics
The integration of cellular connectivity in drones has enhanced forensic opportunities, with some advanced drones using SIM or eSIM technology to connect to cellular networks. In Georgia’s Operation SkyHawk, authorities leveraged cellular data from SIM‑enabled drones along with device metadata from recovered hardware to identify not only drone pilots but also coordination hubs within a multistate smuggling network. [8]
Integrating drone forensics into investigations
Drone forensics enhances traditional investigative techniques by providing actionable intelligence that complements fieldwork. Forensic analysis of flight logs can trace launch and landing sites, guiding investigators to suspects. Communication logs and metadata connect drones to controllers, mobile devices and operators, creating a clear chain of evidence.
Properly preserved digital evidence strengthens prosecutions. Collaboration across agencies further amplifies these efforts, as shared forensic findings help combat the global misuse of drones.
Drone forensics is a rapidly evolving field, blending innovative technology with traditional investigative methods. The continued development of advanced forensic techniques promises to address current challenges and expand capabilities, including innovations like blockchain-based drone registration, AI-driven data analysis and enhanced methods for identifying drones through their unique characteristics.
As drone technology becomes increasingly sophisticated, law enforcement must adapt by prioritizing specialized training, investing in forensic research and fostering collaboration across jurisdictions. These efforts will ensure agencies remain equipped to uncover actionable intelligence from drones, transforming them from potential threats into powerful tools for justice and public safety.
References
- Ludwig K. Sandusky man among 3 accused of using drones to drop drugs, contraband into Ohio prisons. WTOL11. May 2023.
- Boutelet C. Germany concerned about Russian drone overflights of sensitive civilian and military sites. Le Monde. August 2024.
- Ağaci E. Drone sightings over Ramstein raise espionage concerns. Pinnacle Gazette. December 2024.
- Klick A. Lancaster man used drone to deliver fentanyl, other drugs — one user died, prosecutors say. Orange County Register. October 2024.
- Debas EA, Albuali A, Rahman MMH. Forensic examination of drones: A comprehensive study of frameworks, challenges, and machine learning applications. IEEE Access. January 2024.
- US Attorney’s Office, Northern District of Texas. Texas man charged with using drone to deliver contraband to prison. US Department of Justice. August 2022.
- skyCTRL. Anti-drone.
- Balster K. The role of drones and counter-UAS efforts to combat contraband. Correctional News. February 2025.