By Kevin Graves, Chief Technology Officer, IP Fabrics
The increased usage of Internet-based communications such as chat, instant messaging, blogs, VoIP services, and the old standby, email, has placed a new challenge to our technical surveillance teams – how to mine this intelligence source.
The biggest challenge facing our technical investigative teams is that many service providers haven’t complied with the FCC’s CALEA (Communications Assistance for Law Enforcement Act) and aren’t able to execute court-ordered intercepts. As a quick refresher, CALEA is the legislation that requires all telecommunications providers (including ISPs and VoIP providers that have their own servers/equipment) to provide lawful interception assistance to law enforcement. Specifically, CALEA requires these service providers to essentially deliver to law enforcement the data/communications specified in pen register/trap and trace and full content (Title III) court orders. In other words, you present them with the valid court order and they are supposed to send you the intercept data – just like the process for tapping a landline or wireless phone.
This non-compliance problem is most evident with IP-based service providers, and more specifically, smaller ISPs and VoIP providers. When this occurs, the LEA is faced with taking action against the service provider to get them to become compliant (usually very time-consuming), just ignoring the intercept, or providing their own equipment (sometimes called a probe or a tactical intercept system) and executing the intercept themselves – often called a tactical intercept.
Ideally, systems used for this type of tactical intercept have several key features:
1. They Need to be Portable and Remotely Accessible: packaged in a small form-factor such as a rack-mount server or luggable system. The system needs to be easily transported to the service provider facilities and be installed in existing racks, on top of other equipment, or placed on the floor. It should be available with either AC or DC power supplies, and needs to be accessible/managed locally and remotely across a network (e.g., Internet).
2. They Need to be Passive: the probe surveillance interfaces need to be completely passive and not affect the service provider’s network traffic (e.g., don’t add additional latency, don’t degrade signal quality, etc). Also, they need to be identity-free, so they aren’t visible to other devices on the network.
3. They Need to be Intelligent and Self-Contained: The tactical intercept system needs to incorporate the probe/access point, mediation, and administration functions of the typical intercept system – all in a single system. They need to be capable of doing intelligent discovery of targets. For example, they need to be able to discover a target based on a userID, a dynamically assigned IP address, or a phone number. Additionally, they can’t rely on service provider equipment such as routers or session border controllers to perform intercepts.
The VoIP Problem
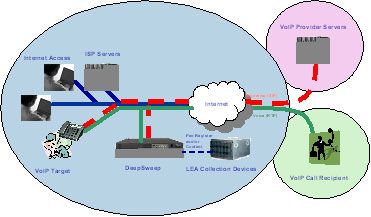 Figure 1: VoIP call setup is often routed differently than the voice |
This last point is a critical one when dealing with VoIP wiretaps, especially in the case on non-managed VoIP services such as those offered by Vonage. In cases like these, there are two key complicating factors. First, inherent in VoIP is the likelihood that the signaling traffic (e.g., SIP) and the encoded voice (e.g., RTP) will traverse different network paths and in most cases both will not be routed through the non-managed VoIP providers facilities (see figure #1).
Without altering the normal network routing (sometimes called a ‘forced routing’) the best place to perform the intercept is close to the user, which is normally at the user’s ISP.
To perform these intercepts, LEAs need tactical intercept systems that can be transported to the target’s ISP, and, these systems need to be capable of intercepting VOIP calls (see figure #2)
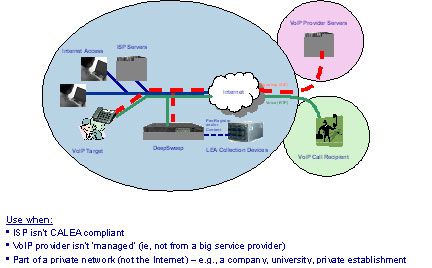 Figure 2: Tactical Internet Wiretap System |
Since the ISP isn’t offering the VoIP service, they most likely don’t have ‘VoIP-aware’ equipment (e.g., session border controller, SIP server, etc) to assist in the intercept. So, the tactical intercept system needs to be completely self-contained and able to discover VoIP calls based on, for example, a phone number, and intercept the call per the court order. Since surveillance court orders are most often pen-registers, the intercept system can’t be simple packet recorder; it must adhere to the electronic surveillance laws and support pen-register, trap & trace, and full content intercepts, as well as deliver the content in ‘near real time’ to support LEA minimization guidelines.
To summarize, Internet-based communications is here today and growing, thus driving the need for Internet intercepts. Barring a change in the FCC’s CALEA enforcement practices, technical investigators will need to be prepared to mobilize and deploy a tactical intercept system (probe) to facilitate these intercepts.











